
Ivan Spiteri
In an era where digitalisation has transformed the way financial institutions work, the security of financial data and transactions is more important than ever. Following a number of security breaches at financial institutions, Swift became concerned about the security of its users. They decided to create a set of security controls and requires all its users to attest their level of compliance with these controls transparently. The CSP is continually updated to address new threats and weaknesses in the ever-changing cybersecurity landscape.
 © by Swift 2024
© by Swift 2024
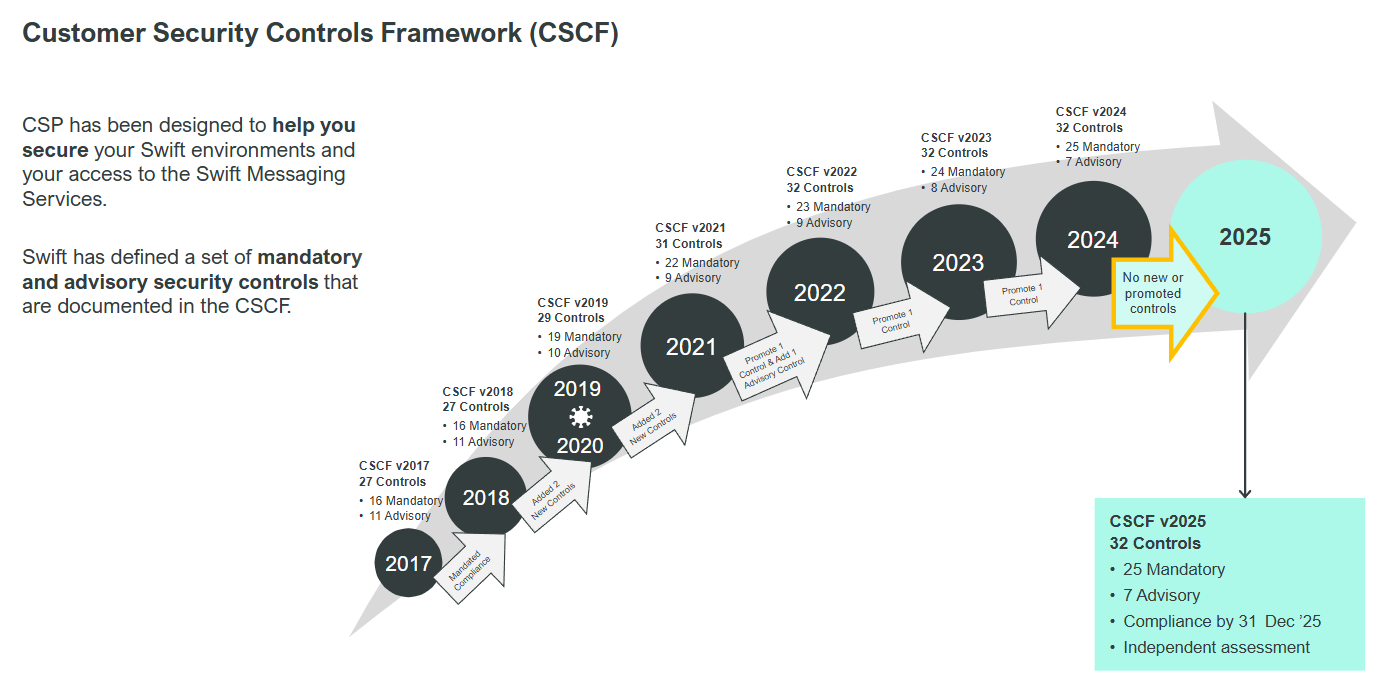
Swift has defined a set of security objectives, which are linked to seven principles and covered by the set of controls in the Customer Security Controls Framework (CSCF). The CSCF consists of 25 mandatory and 7 advisory controls, but not all controls are applicable to all architecture types: it depends on the extent to which an organisation is integrated with Swift systems.
Swift users are required to confirm their compliance with the mandatory security controls between 1 July and 31 December of each year – whether fully compliant or not!

1. Restrict Internet access & segregate critical systems from general IT environment
2. Reduce attack surface & vulnerabilities
3. Physically secure the environment
4. Prevent compromise of credentials
5. Manage identities and segregate privileges
6. Detect anomalous activity to system or transaction records
7. Plan for incident response and information sharing