The EU regulation DORA (Digital Operational Resilience Act) sets a new standard for managing ICT risks. It mandates that significant financial entities conduct Threat-Led Penetration Testing (TLPT) — intelligence-based tests that simulate the capabilities of advanced persistent threat actors (APTs).
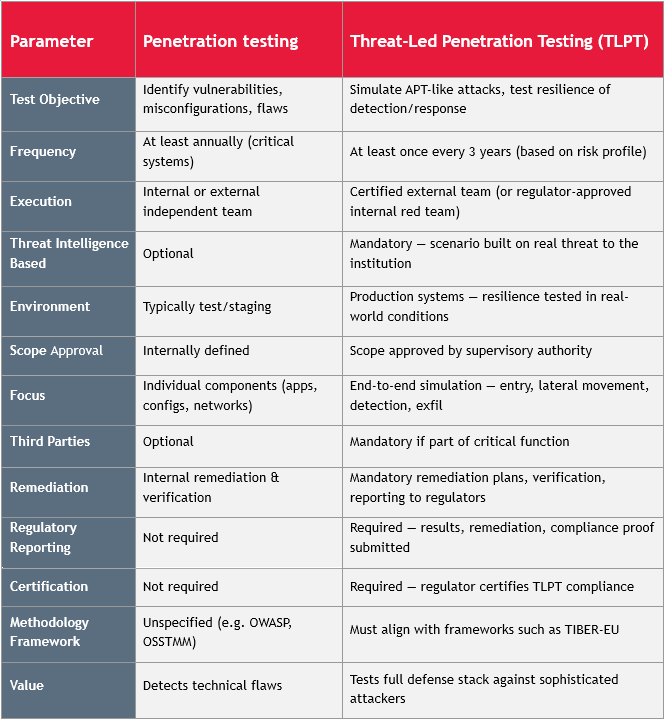
Unlike traditional penetration testing, TLPT aims not only to identify vulnerabilities, but also to validate the organization’s ability to detect, respond to, and recover from a realistic and coordinated cyberattack.
What is TLPT and Why Are Standard Penetration Tests No Longer Enough?
- Full-spectrum attack simulation: intrusion, lateral movement, privilege escalation, persistence, data exfiltration.
- Based on current threat intelligence and sector-specific scenarios.
- Requires detailed scope definition, rules of engagement, identification of critical systems, and test objectives.
Key Differences: TLPT vs. Standard Penetration Testing
What Does DORA Require in Relation to TLPT?
- Tests must reflect the current threat landscape, not a generic scenario
- Scope must include critical functions/systems, the failure of which would impact stability
- TLPT must be performed by external, independent, and certified testers
- Findings must lead to remediation, possible re-testing, and regulatory reporting
For entities under DORA, compliance includes strict control of test frequency, documentation, and communication with authorities (e.g. ECB, CNB). The active red-teaming phase must last at least 12 weeks, to realistically emulate stealthy threat actors.
What are the requirements for testing teams?
DORA also emphasizes the quality and qualifications of entities performing advanced tests. Testers must meet strict criteria, such as:
- They must be renowned experts, with proven technical and organizational skills and specific knowledge;
- Testers must be certified and have completed independent audits or confirmation of proper risk management during testing;
- They must have adequate liability insurance in case of damage caused.
If the institution would like to use its own internal red team, it must obtain the approval of the regulator and ensure the organizational independence of the internal team (avoid conflicts of interest). Operational information about threats for the scenario must be provided by an external provider.