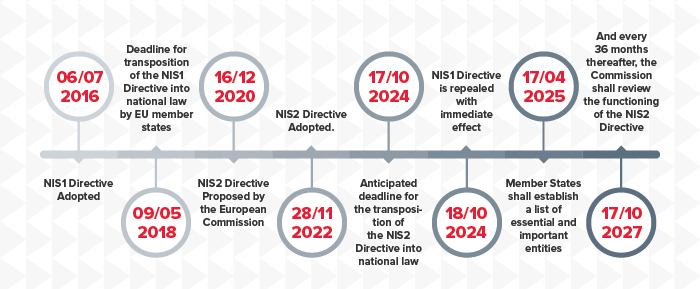
The NIS2 Directive, which will become part of local law transpositions across the EU by October 2024 at the latest, brings new rules and requirements for organisations and aims to strengthen the digital resilience of member states.
What is the purpose of NIS2?
The NIS2 Directive is a comprehensive European Union cyber security legislation aimed at boosting the overall level of cyber security within the EU through legal measures. It aims to harmonise and enhance the cyber security of member states across certain sectors and essential businesses within the EU.The NIS2 Directive, following up on its predecessor, aims to achieve the three following goals:
- Setting the bar for cyber security measures in critical industries through a significant expansion of the in-scope organisations compared to NIS1
- Ensuring that the cyber security posture across the different EU member states and national governments significantly improves
- Strengthen the EU cooperation between the cyber security authorities
Who is subject to the Directive?
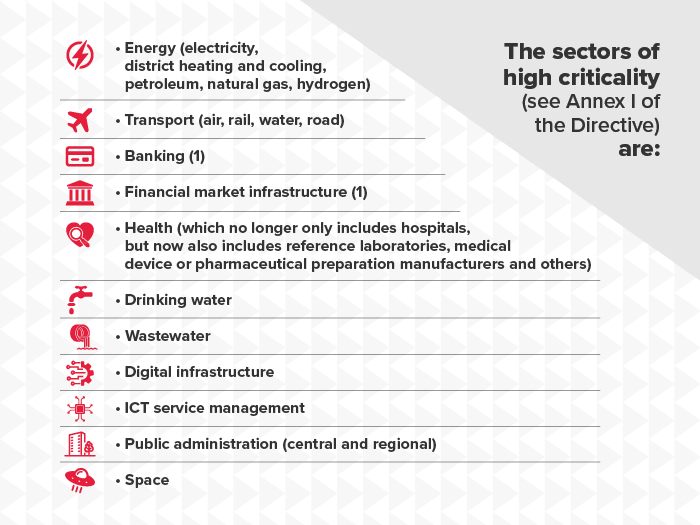
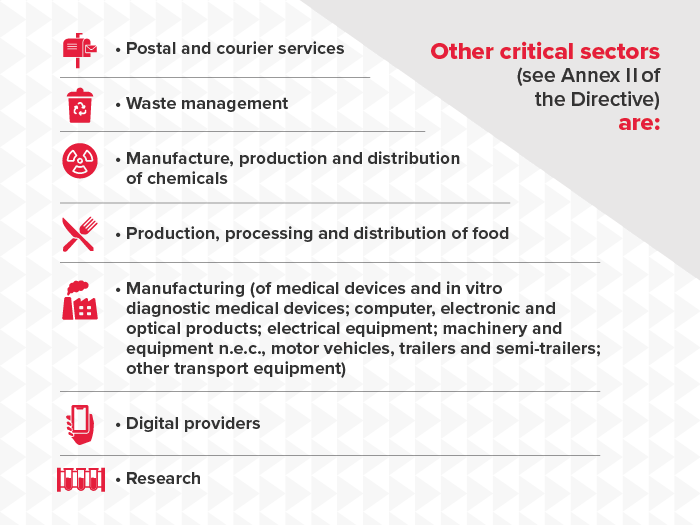
The Directive applies to businesses within EU borders or those providing their products or services within the Union. NIS2 significantly expands the scope of sectors, categorising the 18 sectors into ’Very Critical' and 'Other Critical' sectors based on factors such as size, sector and criticality. Entities that exceed the threshold for medium-sized enterprises, i.e. those with 50 or more employees and an annual turnover of more than €10 million or an annual balance sheet total of more than €43 million, are generally covered by the directive. Small and micro businesses are not covered unless they are covered by an exemption. By December 2024, the national cyber security authorities of the EU member states will have defined and set the definitive requirements of organisations expected to comply with the Directive and will require registration of all Essential and Important entities.
Overlap with the Digital Operational Resilience Act (DORA)
To ensure a harmonious implementation, the European Commission has issued Guidelines clarifying the exemption of entities to which sector-specific legal acts apply from the NIS2 Directive (read our article about the relationship between DORA & the NIS2 Dirtective). These Guidelines explicitly state that DORA has priority over NIS2 provisions on ICT risk management, cyber incident reporting, digital operational resilience testing, information-sharing, ICT third-party risk, supervision, and enforcement. DORA incorporates a provision known as "lex specialis," granting it priority over the NIS2 Directive, which is considered a general law. This provision ensures that if there are any conflicts or overlaps between the two directives, DORA takes precedence. The "lex specialis" provision in DORA helps to avoid confusion and ambiguity in the regulatory landscape.
How does NIS2 affect your organisation?
If you are covered by NIS2, you must implement appropriate and proportionate technical, operational and organisational measures to manage the risks and prevent or minimise the impact of incidents associated with the systems supporting socially critical services. Regulations bring not only challenges and investment towards compliance but also opportunities: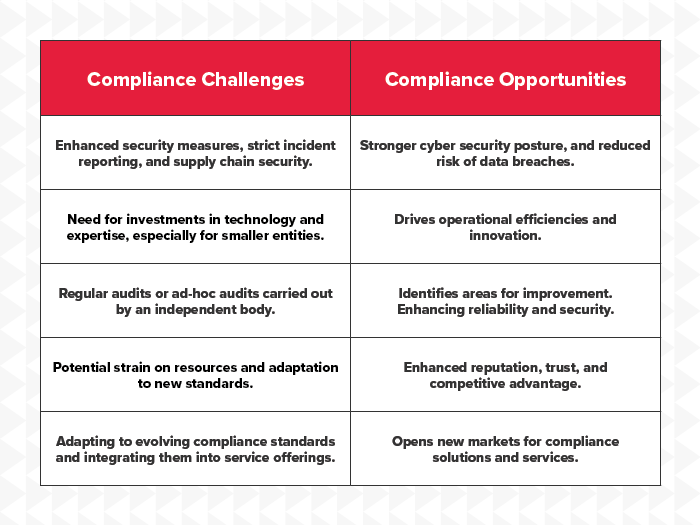
Overall, organisations must establish effective processes for risk management, incident management, supplier management, governance and management involvement. Such measures shall be based on a risk-based approach aimed at protecting the network and information systems, as well as the physical environment of those systems, from incidents and shall include at least the following:
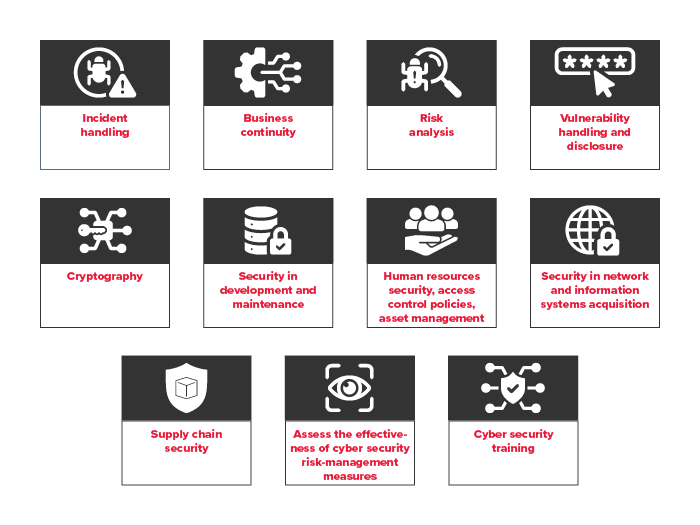
NIS2 requirements for organisations
Management accountability
- Management needs to be more involved in approving cyber security risk management measures. In addition, management must also oversee the implementation of measures and be accountable for the organisation's non-compliance. Management must also have the necessary training and knowledge to identify risks, assess actions and impact on the mission-critical service.
Reporting obligations
- In connection with the NIS Directive, national Competent Authorities (CAs) and Computer Incident Response Teams (CSIRT) were established to be notified of significant incidents on a national level.
- Organisations covered by NIS2 must report significant security breaches within 24 hours of discovery to relevant authorities. Within 72 hours, they must evaluate the severity of the incident and indicators of compromise. A final report with assessment and conclusion must be submitted within one month.
- An incident is considered material if the incident or cyber threat (i) has caused or has the potential to cause significant supply or operational disruptions or financial losses to the entity, or (ii) the incident has affected or may affect other natural or legal persons by causing significant material or immaterial losses.
What are the consequences of not complying with NIS2 requirements?
Covered entities can expect competent national authorities to conduct oversight through audits, on-site inspections and requests for evidence of NIS2 compliance. For essential entities, proactive supervision will be conducted, while for important entities, follow-up supervision will continue to be conducted if an incident occurs. If the entity does not fulfil the requirements of NIS2, the authorities may impose administrative fines, with critical entities being subject to a maximum of at least €10 million or at least 2% of the total global annual turnover of the previous financial year. In addition, management may be held accountable on bread where sanctions in the form of temporary bans on management functions or temporary suspension of services.How can BDO help?
For many organisations, complying with the requirements of the NIS2 directive can seem like a daunting task Our cyber security experts not only assist you in becoming NIS2 compliant, but we also transform this challenge into an opportunity to enhance your overall security and resilience. We can support your organisation by:- Leverage industry standards and best practices – we utilise renowned industry standards and frameworks to perform comprehensive assessments that are tailored to your specificities and needs.
- Improved cyber resilience - together we strengthen your organisation’s ability to detect, respond, and recover from cyber incidents effectively, minimising the impact for to your operations.
- BDO brings a fresh and unbiased perspective to evaluate your cyber security infrastructure, ensuring a comprehensive and impartial analysis.
- Our team of consultants are seasoned experts in cyber security, well-versed in the latest threats, vulnerabilities, and best practices.
What you can expect from us
- Customised cyber security maturity assessment – our team conducts a thorough evaluation of your current cyber security posture based on and aligned with industry standards and sector-specific best practices.
- Gap analysis – identify weaknesses and vulnerabilities in your existing cyber security organisation, identifying ‘must have’s to ensure NIS2 compliance in your jurisdiction but also ‘nice to haves’ based on your desired security level.
- Customised action plan – together with you we create a tailored action plan with clear, concrete and actionable steps to improve your cyber security posture and resilience.
- Implementation support – our experts guide your team in implementing the recommended security measures to ensure better protect your organization and ensure NIS2 compliance. E.g.
- Management accountability and training: define management responsibilities and awareness training to the Board.
- Third Party Risk Management: identify relevant suppliers, assess potential security risks and exercise oversight on critical suppliers.
- Contingency planning: we can help you create a contingency plan and develop and test procedures in the event of a (simulated) incident.
- Incident reporting: incident handling and reporting procedures
.png)
.png)