DORA: Understanding RTS for Third-Party Risk Management
DORA: Understanding RTS for Third-Party Risk Management
One of the foremost regulatory goals for DORA is the assessment and ongoing monitoring of risks arising from those business relationships. The RTS sets out guidelines and requirements that financial institutions (FIs) must adhere to when engaging ICT third-party service providers (TPS).
In June 2023, the first wave of Draft RTS (Regulatory Technical Standards) and ITS (Implementing Technical Standard) was published by the European Supervisory Authorities. The objective of these additional Policy Products is to provide detailed specifications and guidelines on how certain provisions in the basic legislative Act should be implemented across the EU. The first batch of Policy Products are Draft and have been published for consultation consists of:
- RTS to specify the policy on ICT services performed by ICT third-party providers (Article 28(10))
- RTS on criteria for the classification of ICT-related incidents (Article 18(3))
- ITS to establish the templates for the register of information (Art.28(9))
- RTS on ICT risk management framework (Article 15) and RTS on simplified ICT risk management framework (Article 16(3))
Let’s dive deeper into the contents of the RTS, specifying the policy on ICT services performed by ICT third-party providers.
RTS on ICT third-party provider management
The financial industry has been increasingly dependent on Information and communication technology (ICT) service providers for various business functions. One of the foremost regulatory goals for DORA is the assessment and ongoing monitoring of risks arising from those business relationships.
The RTS sets out guidelines and requirements that financial institutions (FIs) must adhere to when engaging ICT third-party service providers (TPS). The DORA regulation (article 28.2) states that financial entities should:
- perform regular reviews of their strategy for using third-party ICT providers.
- take the use of crucial ICT services into consideration, which are supported by those providers.
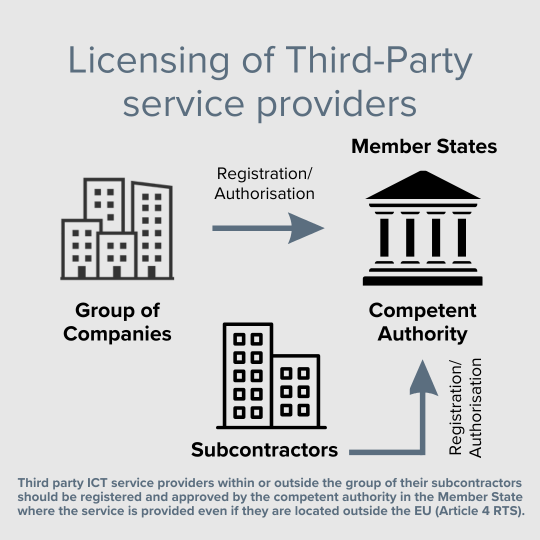
On top of this, the RTS establishes the following set of principles for a TPS policy:
- Consistent and coherent application within the group and its subsidiaries
- Definition of review frequency to keep an eye on ICT risk
- Definition of internal representative for managing ICT-related risks.
- Focus on risks for the entire life cycle of ICT contract management (including due diligence, change management).
- Evaluation criteria for ICT third-party service provider (e.g., business reputation, technical resources, information security posture, governance, internal controls).
- Rights to inspection, access to information and termination process.
LIFE CYCLE – ICT SERVICES
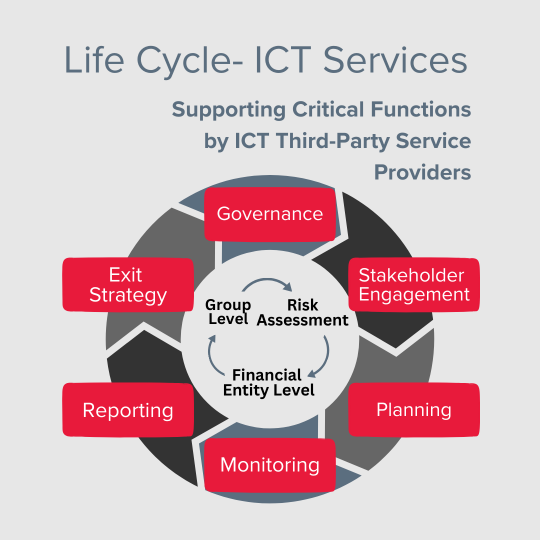
ICT Third-Party Risk Management
RTS Conclusion, Challenges and Support
The relationship between the financial sector and third-party ICT service providers is a significant area that requires special attention while implementing DORA. The RTS therefore requires strategy and policy which should:- be proportionate to the size, nature, scale and complexity of the financial entity and the criticality of the functions supported by the ICT services provided by the third-party service provider,
- be integrated into the overall risk management framework of the financial entity,
- include a risk assessment of the ICT third-party service provider,
- include a due diligence process for selecting an ICT third-party service provider,
- include provisions for monitoring and reviewing the performance of the ICT third-party service provider, and
- include provisions for terminating or replacing an ICT third-party service provider.
Challenges
Following are the common challenges faced by the financial sector while going through the implementation of RTS for ICT third-party risk management.- Co-operation with the competent authorities (e.g. US-based entities)
- Effective access to data and premises for FIs, Auditors and Competent Authorities
- Frequent changes in regulatory requirements
- Scalability
- Costs
- Change management
- Compatibility issues
- Data privacy
- Information Security requirements
- Capacity Management
BDO Malta: Your Trusted Partner for DORA Compliance
The RTS addresses the complete life cycle of ICT third-party risks. The continuous growth in threats for unanticipated occurrences have prompted businesses to prepare for such disasters, which often emerge as a result of weaknesses in governance, pitfalls in strategy, risk identification and mitigation.
The European Union has set January 17th, 2025 as the deadline to achieve DORA compliance. While this might seem a distant target, in fact achieving DORA compliance is a very complex and challenging task which requires a concerted effort by the in-scope financial entities. At BDO Malta, we understand the profound impact that the journey towards DORA compliance has on such organisations. Our team of regulatory and compliance technical experts is dedicated to helping your company navigate this complex environment. Our comprehensive range of services includes:
- Board and Management Training on DORA;
- Expert guidance on DORA compliance;
- Performing gap analyses;
- Conducting risk assessments;
- Developing and implementing incident management and business continuity plans;
- Providing continuous support and monitoring.
Get in touch
